Over the weekend, hundreds of thousands of computers around the world were hit by a large-scale ransomware attack. The operation relied on a variant of the WannaCry malware, a tool included in a hacking arsenal leaked by the Shadow Brokers last month.
The hacking group said they stole the files from the National Security Agency, and that the April release was just a part of a larger vault of tools they are sitting on. The ones responsible for the WannaCry attack, however, remain unidentified.
U.S. authorities and security agencies around the world have also confirmed that the attack has hit services in their countries. Businesses and institutions are worried about facing a threat on Monday when they resume commercial activities.
What is WannaCry and how does it work?
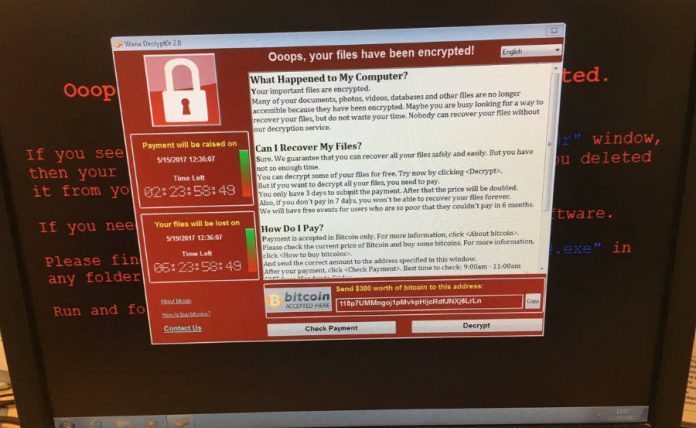
The tool used by hackers to take down systems worldwide is a variant of the WannaCry tool, also known as WCry or Wana Decryptor. It has been distributed via email as far as authorities know, and all it takes is one person to open it to compromise entire networks.
This category of malware, known as ransomware, gets its name because its objective is to get you in a position where you have to pay ransom in exchange for access to your computer or files.
In the case of this weekend’s attack, WannaCry encrypts the system’s data and requests $300 in Bitcoin for the program to decrypt them and let users access them again. Hackers give a three-day lapse to pay or else, the ransom amount will double and so on.
Analysts suggest the attackers made it decryption-proof, as some tech-savvy users might try their hand at using software to bypass making any payments.
Which countries have been affected by WannaCry ransomware?
As of now, there have been over 200,000 computers affected by the ransomware, as it spreads across the entire network after a single user receives an email with the malware. Roughly 100 countries have confirmed WannaCry has hit some of their institutions.
The attack exploits a vulnerability found in Windows XP and later versions, but Microsoft issued a patch that deals with these security holes a couple of months ago. It took analysts by surprise the sheer amount of units that had not installed the update.
Among the most notorious networks affected are those of the National Health Service in the United Kingdom and the Interior Ministry in Russia. In British hospitals, doctors were locked out of patients’ files and records, thus severely limiting their operations.
Thailand #WannaCry #Ranswomware #CyberSecurity pic.twitter.com/uFfT99bv0x
— James McL 🏴 🇹🇭🇺🇦 🇳🇿 (@JamesMcLeirigh) May 14, 2017
Companies like the American courier service FedEx and the French automaker Renault have also been hit. Other targets include some Asian university networks, the German transportation system, and the Spanish telecom company Telefonica.
While authorities handle no evidence of data theft yet, some analysts suggest that users may be forced to comply in cases like Britain’s NHS. This could lead to a potential $1 billion in ransom collected when the three-day deadline arrives.
The cyber criminals and authors of the WannaCry attack have yet to be tracked down. Its impact was such that it made Microsoft make a rare move and issue further patches to Windows XP, a platform that has been unsupported since 2014.
Security agencies are working together with public and private entities affected by the ransomware, in some cases shutting down entire systems to prevent the threat from spreading. As of now, there is no official confirmation of entities paying up or people harmed as a result of network outages.
Source: The New York Times










